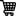Zombie Army
In May 2012, the hacktivist group “Anonymous” which had weighed in favour of Anna Hazare’s campaign, was in news because it again launched distributed denial of service (DDoS) attacks against Indian websites. (Kindly refer to Module 2 of Mains GS).
We should note that DDoS is not actually hacking the website but is a common technique used to temporarily bring down websites. DDoS attacks are well-orchestrated ones on Web servers of a website, and on the domain name servers. The idea is to flood the servers with a humongous number of requests, resulting in the temporary outage of a website or shutdown of the servers. Once this is accomplished, the incoming traffic can be redirected to an intermediate page, where often the perpetrators of these attacks post their messages explaining the reason for why the website has been targeted.
DDoS attacks can cause temporary outage to legitimate users because the attack has occupied a major chunk of network bandwidth and server resources, and in many cases, it may cause the websites to go offline as the Web servers can shut down.
Internet security companies perceive botnets, or zombie army attacks, to be more dangerous than viruses, worms or spam on the Web. These attacks cripple website and, therefore, the services these sites offer, which results in losses. Many companies invest heavily in protection infrastructure. However, even with the most secure carapace, hackers and crackers have been able to work their way around it. (Source: The Hindu)
Anatomy of DDoS
DDoS attacks can be understood by imagining a pyramid-like structure, comprising a series of chain reactions on computer networks. At the top of the pyramid sits the hacker or the cracker, instigating these DDoS attacks. The hacker’s machine sends out electronic commands to a layer of machines — called ‘zombie computers’ or bots — which are part of these attacks. Some of these are voluntary zombies, while others are hapless machines that have been compromised and are being used as part of the ‘attacking’ network. This layer of computers, in the pyramid, that receives commands from the attacking hackers/crackers are called the ‘zombie army’ or botnet.
The zombie army launches the real attack on the target website or server, by routing the requests via another layer of innocent computers called the ‘reflectors’. So to the Web server that hosts the site under attack, these requests, emanating from ‘innocent’ reflector computers appear harmless, and servers try to cater to their requests, falling prey to the attack.